
A flaw, or perhaps a design decision, in GitHub is exploited by threat actors to distribute malware using URLs associated with Microsoft repositories, making the files appear to be trusted.
Although most of the malware activity is based on Microsoft GitHub URLs, this “flaw” can be exploited on any public repository on GitHub, allowing attackers to create very convincing decoys. Become.
Abusing GitHub’s file upload feature
Yesterday, McAfee released a report about a new LUA malware loader distributed through what appears to be a legitimate Microsoft GitHub repository for “C++ Library Manager for Windows, Linux, and MacOS” known as vcpkg.
Although the malware installer URLs shown below clearly indicate that they belong to the Microsoft repository, we could not find any references to the files in the project’s source code.
https://github[.]com/microsoft/vcpkg/files/14125503/Cheat.Lab.2.7.2.zip
https://github[.]com/microsoft/STL/files/14432565/Cheater.Pro.1.6.0.zip
Thinking it strange that a Microsoft repository has been distributing malware since February, BleepingComputer looked into it and found that the file was vcpkg However, it was uploaded as part of a comment left on a commit or issue within a project.
When leaving a comment, GitHub users can attach files (archives, documents, etc.). The file is uploaded to her GitHub CDN and associated with the associated project using a unique URL of the form:https://www.github.com/{project_user}/{repo_name}/files/{file_id}/{file_name}.‘
For videos and images, files are saved to: /assets/ Pass instead.
Instead of generating a URL after posting a comment, GitHub automatically generates a download link when you add a file to an unsaved comment, as shown below. This allows an attacker to unknowingly attach malware to any repository.
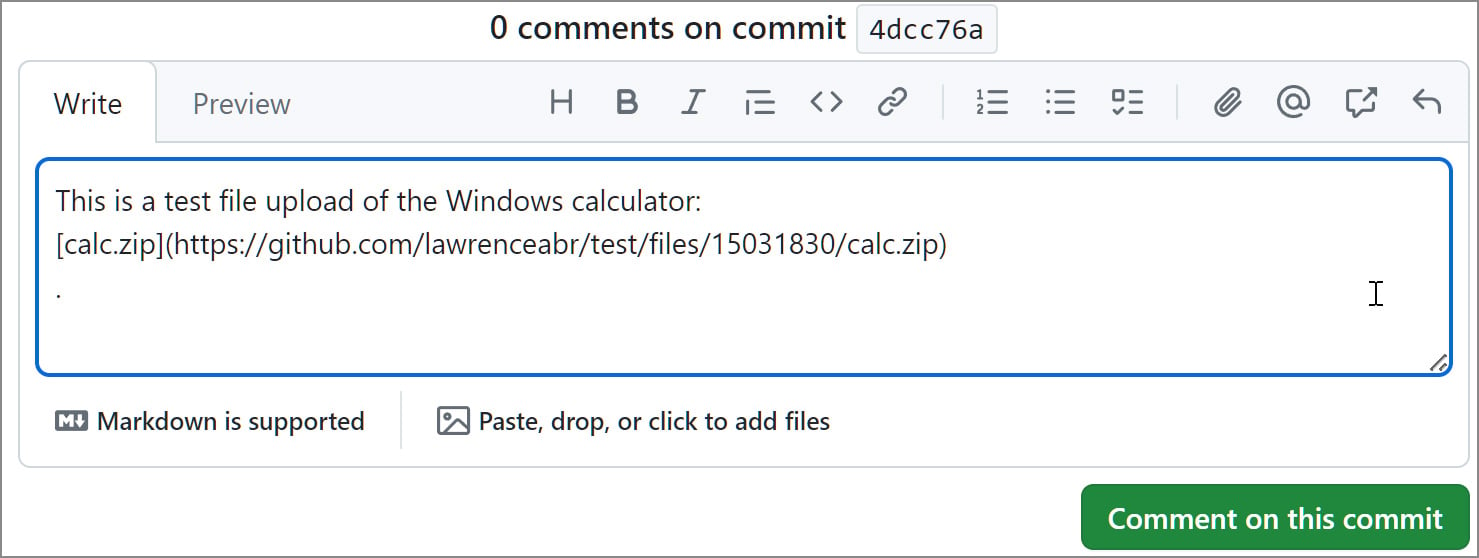
Source: BleepingComputer
If you don’t post a comment or decide to delete it after posting it, your file will not be removed from GitHub’s CDN and the download URL will continue to work forever.
Because the URL of the file includes the name of the repository in which the comment was created, and almost all software companies use GitHub, this flaw could allow attackers to develop very crafty and reliable decoys. There is a gender.
For example, a threat actor might upload a malware executable to NVIDIA’s driver installer repository that pretends to be a new driver that fixes an issue in a popular game. Alternatively, an attacker could upload the file in the comment to the Google Chromium source code and pretend it is a new test version of the web browser.
These URLs look like they belong to your company’s repository, which gives them a lot more credibility.
Unfortunately, BleepingComputer was unable to find any settings that would allow companies to manage files attached to their projects, even if they learned that their repositories were being exploited to distribute malware.
Additionally, disabling comments is the only way to protect your GitHub account from such abuse and reputational damage. According to this GitHub support document, you can only temporarily disable comments for up to six months at a time.
However, restricting comments can have a significant impact on the development of your project, as users will not be able to report bugs or suggestions.
Just last month, Sergey Frankov of UNPACME, an automated malware analysis service, livestreamed the bug on Twitch and said that attackers are actively exploiting the bug.
Weeks later… GitHub bug still drops malware pic.twitter.com/s165zOAsoI
— Herrcore (@herrcore) March 27, 2024
As part of our investigation into this bug, BleepingComputer was able to locate just one repository, httprouter, that was exploited to distribute malware in this manner. It was “Cheater.Pro.1.6.0.zip”, the same one you see in Microsoft’s URL.
However, Frankoff told BleepingComputer that he discovered a similar campaign in March that leveraged the same LUA loader malware called SmartLoader disguised as Aimmy cheat software.
Frankoff told BleepingComputer that SmartLoader is typically installed along with other payloads, such as information-stealing malware RedLine.
BleepingComputer contacted both GitHub and Microsoft about the exploit on Thursday, but did not receive a response.
As of this article’s publication, information-stealing malware is still being distributed through links associated with Microsoft’s GitHub repositories.

